FLARE VM: The Windows Malware Analysis Distribution You've Always Needed! | Mandiant | Google Cloud Blog

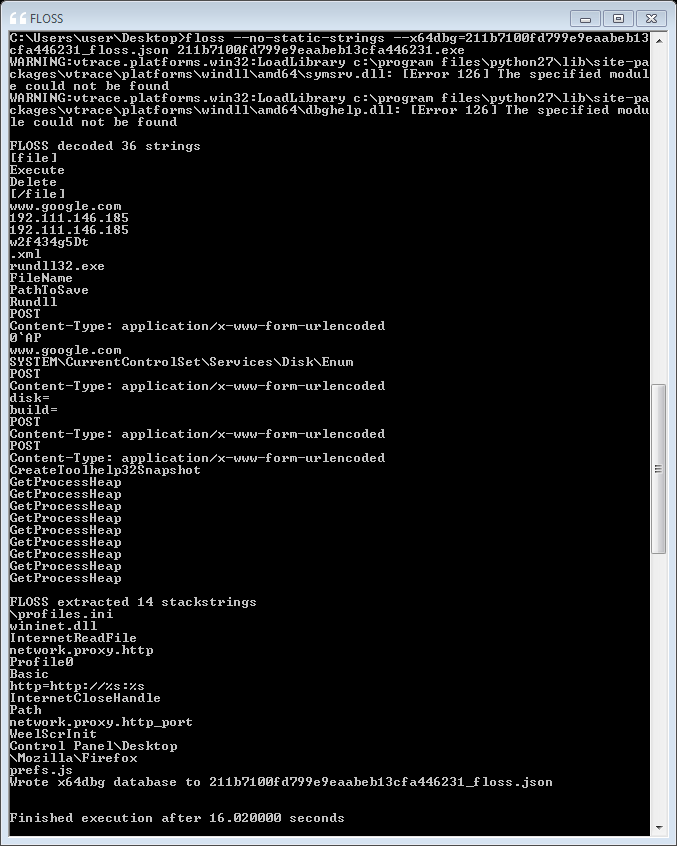
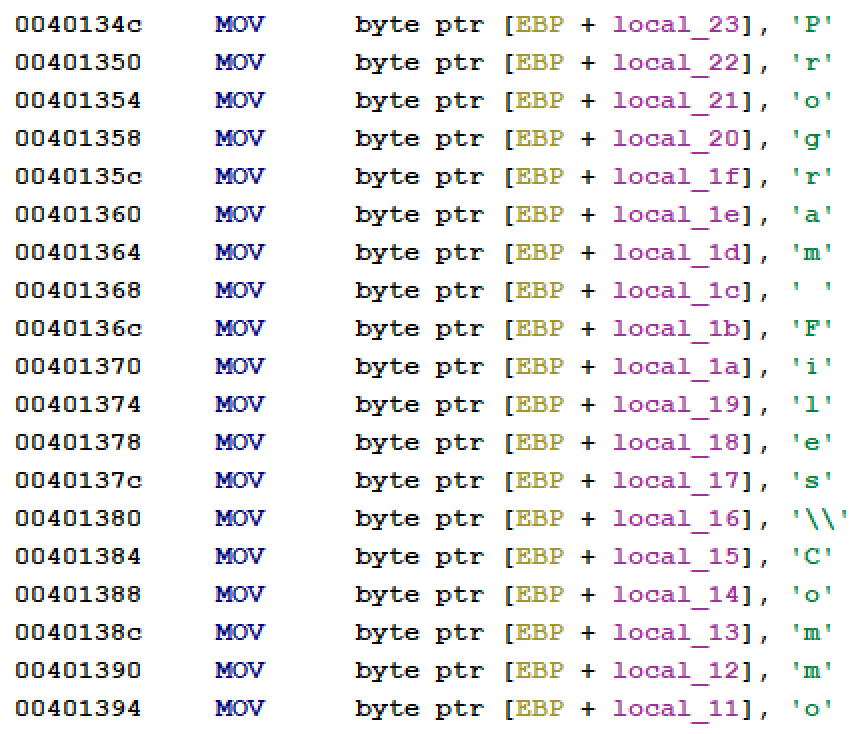
Automatically Extracting Obfuscated Strings from Malware using the FireEye Labs Obfuscated String Solver (FLOSS) | Mandiant | Google Cloud Blog

Automatically Extracting Obfuscated Strings from Malware using the FireEye Labs Obfuscated String Solver (FLOSS) | Mandiant | Google Cloud Blog

FLARE VM: The Windows Malware Analysis Distribution You've Always Needed! | Mandiant | Google Cloud Blog
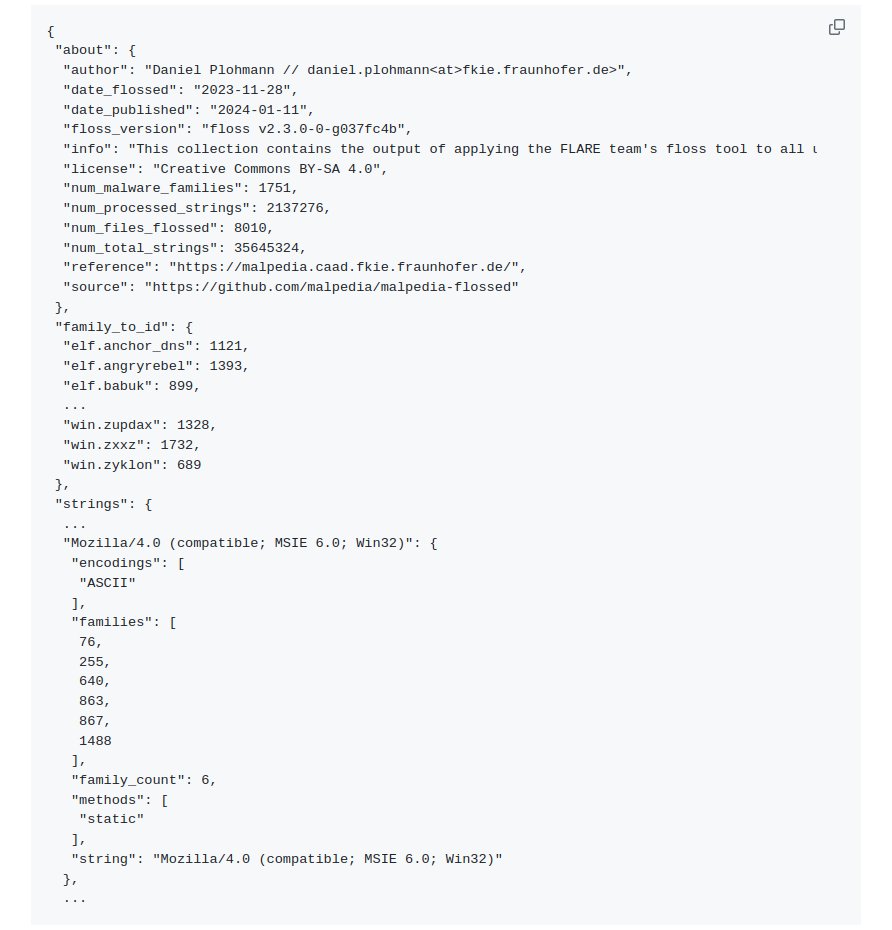
Malpedia on X: "🛠️ We just published "Malpedia flossed": @Mandiant FLARE team's floss tool applied to all unpacked + dumped samples in @malpedia. Results: 35.645.324 raw strings, distilled to 2.137.276 unique strings


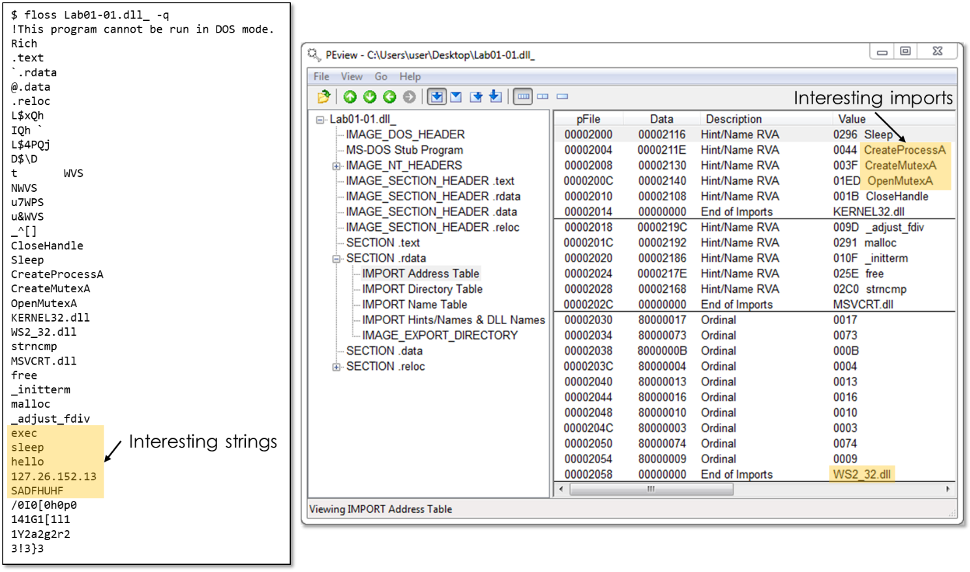



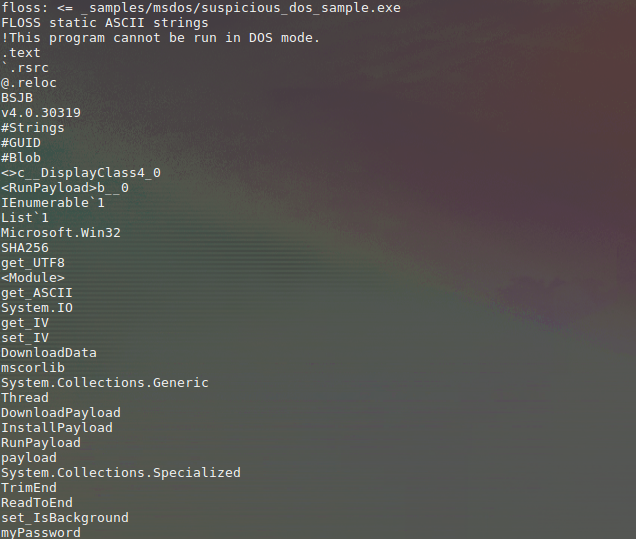



![Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak](https://miro.medium.com/v2/resize:fit:1400/1*AQG8iPfpWsyaMviqfQs4JQ.png)


.png)